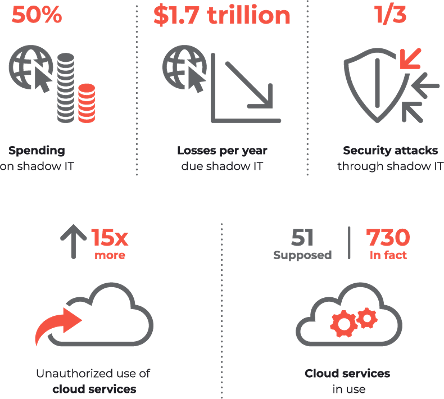
Here’s a growing trend creeping into organizations of all industries and sizes: Shadow IT. Shadow IT is the use of information technology systems, devices, software, applications, and services without explicit IT department approval. It has grown exponentially in recent years with the adoption of cloud-based applications like Dropbox or surveys such as Zoomerang. The list goes on and on.
So what’s the problem? For starters, if you’re in a highly regulated industry like medical or financial services, you’re almost guaranteed to be flagrantly violating data privacy laws or at least flirting with them; and if you’re audited, you could end up facing BIG fines, not to mention legal fees and bad PR. Second, the barrier to entry is LOW. Anyone with a browser and a credit card can purchase or enroll themselves into applications that integrate with your organization’s critical applications and/or store company data such as client lists, e-mails, files, etc.
Of course, not all cloud apps are bad, but you as the owner and your IT person or company need to at least be AWARE of these applications to determine if they’re a threat to security or a violation of data privacy laws, and simply to keep your confidential information, well, confidential!
For starters, your IT company or person should be constantly monitoring your network for new and unknown software or devices. This can (and should!) be incorporated into routine vulnerability testing. If you’re not sure this is being done now, find out. As Intel founder Andy Grove once said, “Only the paranoid survive.” Once you know what applications are being used, you can set your company firewall to block applications you DON’T want employees to access with company data and devices, and allow those that are company-approved.
Also, make sure you catalogue these sites somewhere by user with the login information for that person. If an employee leaves your organization or is fired, they may remember what the username and password are to these cloud applications and could use them to harm your organization or steal data to sell or give to a competitor. Don’t put yourself at risk!