Anyone who has a small to medium-sized business has “an” IT plan, but per a recent study, only 14% of them rate their own cybersecurity plans as “effective.” This is alarming when you consider that 43% of small businesses are targeted by cyberattacks. It’s like having a rowboat with leaking life vests because you don’t really believe your boat can sink; only yachts sink, right?
Patch up those floaties, it’s going to be a long ride. You don’t want to be one of the 60% of small businesses that have to close their doors forever following a single cyberattack.
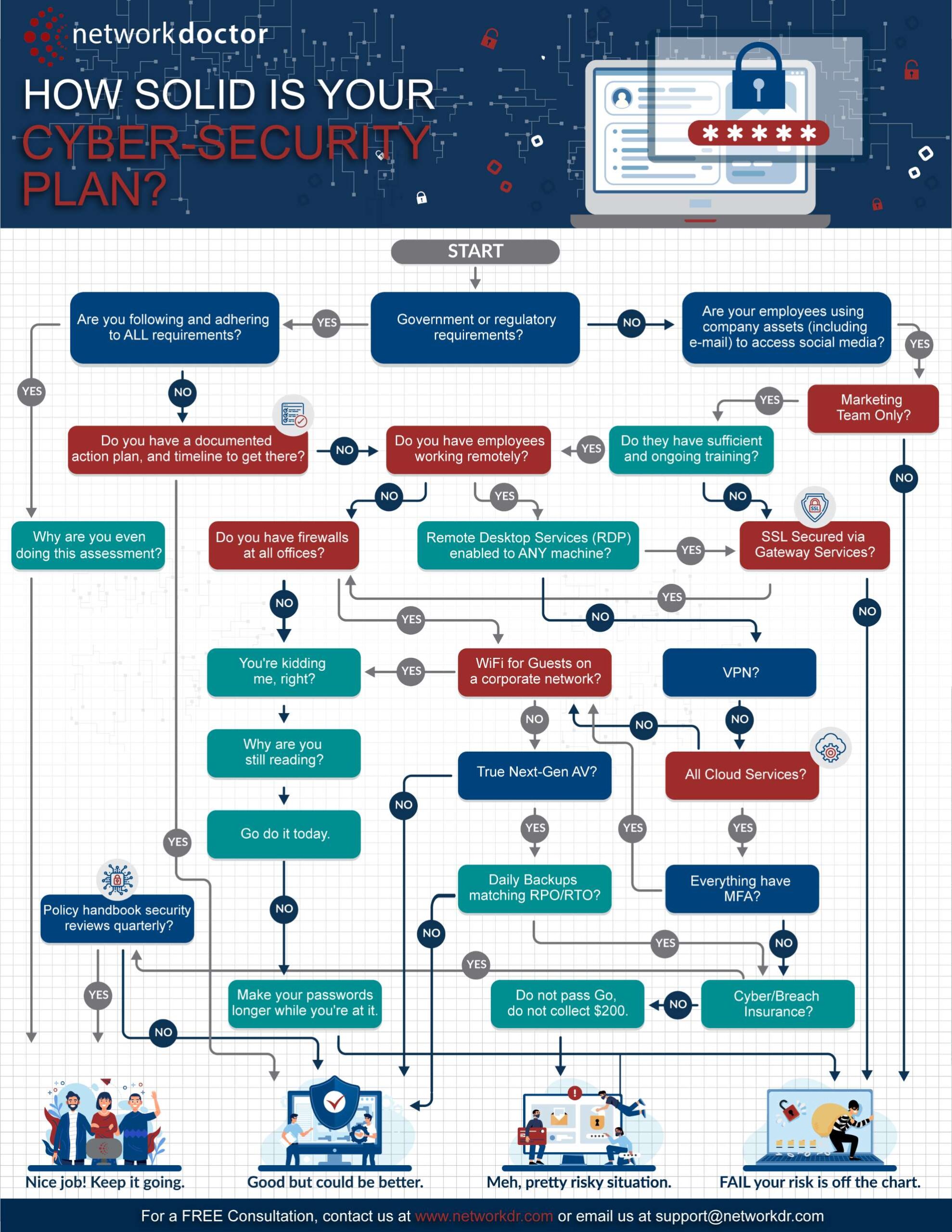
Let’s look at your cybersecurity plan. Does it have the elements you need to keep floating, or will one mistake send you to the bottom of the lake?
How Solid is Your Cybersecurity Plan for Meeting Compliance Issues?
In case you missed it, compliancy is kind of a big deal these days. Governmental regulatory standards are tightening as they hold businesses accountable for client privacy.
If you are found to be in violation of these industry standards, you are looking at stiff fines and lawsuits. Many of these violations can be avoided by proving you have your business’ data secured under an effective cybersecurity plan.
The health agency has more hoops than other agencies, with rules ranging from HIPAA to the HITECH Act.
Meanwhile, law firms answer to the BAR association, and financial institutions face the BSA AML, FACTA, and the GLBA.
These are all before you even factor in state regulations and good common-sense best practices. If you don’t understand the regulations governing your small to medium-sized business, you may need to hire a professional who does. When it comes to compliance issues, what you don’t know will hurt you.
Documenting Your IT Plan is More Important Than You Realize
It’s not enough to buy some boxed anti-virus software and call it a day. You need to have your complete cybersecurity strategy documented. If a governmental agency randomly chose your office for an IT audit ensuring compliance, how can you prove that you are taking the necessary steps?
In addition to documenting the plan itself, document your backup and recovery plans and your Business Continuity Plan as well, and document all routine testing. Like those life vests stored under your boat’s seat, you don’t want to wait until you’re sinking to find out how leaky they really are.
How Solid is Your IT Plan for Remote Workers?
It’s a pretty good bet that at least some of your remote workers will continue to work remotely now. How are their devices secured? Are you providing them the tools they need to protect your network like email safety rules, an Acceptable Use Policy, and cybersecurity awareness training?
Are your password requirements strong enough, and do they discourage the repetition of passwords? Do you require a multifactor log-in process for an added layer of security?
Your remote workers are a special “breed” of vulnerability. They tend to be laxer about security, log into unsecured WIFI networks, allow family and friends to use their devices, “cheat” on passwords, remain logged in, store files directly to their PCs, and other risky practices.
Using a VPN and switching to cloud services is a good start for beefing up your cybersecurity strategies when working remotely.
Speaking of Documentation, Do You Have Clear Written Policies for Employees?
Your employees are your first line of defense. Cybersecurity rests at their fingertips. Do they know that using email for personal reasons or using personal devices may expose your network?
Having clearly defined policies such as BYOD policies, remote workforce guidelines, and Acceptable Use Policies will protect your network and your reputation.
It’s important to keep signed policies in employee files. If the unthinkable happens and an employee accidentally launches malware into your network, having a signed policy in place:
- Helps prove to regulatory agencies that you took appropriate actions to avoid the breach
- Closes loopholes from cyber risk insurance companies looking for a way to get out of paying your claim
- May help limit monetary damages for lawsuits by proving that you took reasonable precautions prior to the breach
Employee policies should be renewed as your office tech changes and made a part of your new employee onboarding process.
Some things covered in these policies would include who, what, when, where, and how:
- Who has access to devices?
- What are the permissions required for the user to perform their job?
- When can a user use a personal device rather than a work-issued device?
- Where is it appropriate for the employee to use the device? (secured WIFI access spots only, for instance)
- How is the device secured to protect your network?
network doctor Can Help
Cybersecurity threats to small and medium-sized businesses are increasing in both number and sophistication, and it’s imperative that your cybersecurity plan can meet the rising challenge. Even if you have strategies in place, it never hurts to have a second opinion (especially a free one). Schedule your no-cost, no-obligation network assessment, and complementary dark web scan today to ensure your organization has a secure tomorrow.
Next step: What business executives want to know about cyber risk
Let Network Doctor give you the answers you need to get started on solidifying your IT plan.